Using a cache of leaked passwords and website information, academics at Virginia Tech and researchers at Dashlane have produced a report all about bad password habits. You can read the full report on a pdf here: https://people.cs.vt.edu/gangwang/pass.pdf
We've summarised some of the most common password setting habits they saw.
So what was measured?
In total the report includes data for 28,836,775 users and their 61,552,446 passwords. The researchers matched the user ID (email address) and passwords contained in 107 leaked data sets spanning 8 years.
The researchers wanted to use empirical evidence rather than relying on interviews or questionnaires because 1) the sample size would be too small and 2) their answers may not accurately reflect their real online habits.
Let's Summarise
-
People re-use their passwords across several services
-
Password re-use is common even after a breach
-
Modified passwords are really predictable
One password for several services
The researchers found that a large number of users included in the data used the same password or set of passwords across multiple websites and online services. Around 38% or 10.9 million users used the same password at least twice. That probably doesn’t come as a surprise to most of you. Who hasn’t used the same password for a few websites before?
It seems that for most people the convenience of having one or two passwords to remember outweighs the potential risk of having one of your accounts hacked, thus giving the cyber criminals access to more of your accounts.

Re-Using passwords after a breach
If you knew that one of your accounts had been hacked, would you change your password for the other online services that use the same password?
The researchers found that 70% of users who appeared in the data sets were still using the leaked password for 1 year after the initial breach. 40% of users were still using the same password 3 years after the breach.
But why? Of course it is possible that the users didn’t know their data had been breached. Some companies are lax at notifying their users of a breach, or perhaps the user ignored the notification. Another possibility is that users didn’t think that just because one account had been breached their other accounts would be vulnerable.
There is little to stop a cyber criminal from searching through these leaked data sets and attempting to log-in to other services to steal your data or use your stored payment details.
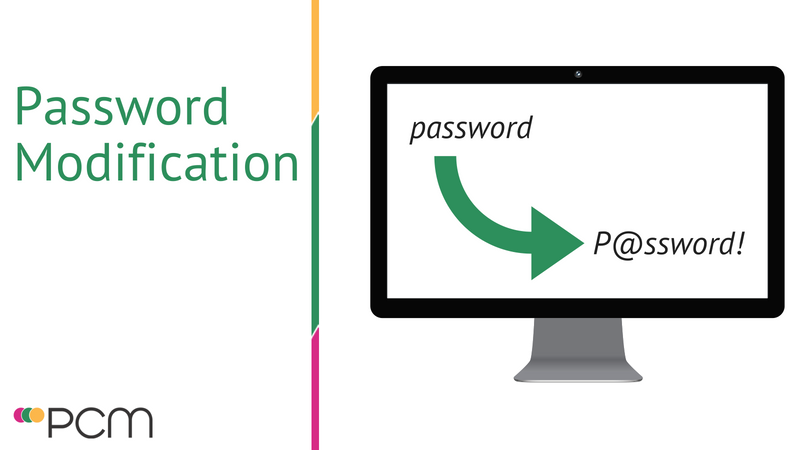
Password modifications are easy to guess
If the user wasn’t using the exact same password, then a lot of them were using modifications to the same password rather than something completely different. The researchers found some common modifications across the datasets including:
Capitalisation: One or more of the letters in the original password would be modified by making it a capital letter so password becomes Password
Sub-string: Additional data would be added at the end of the password. So password becomes password123
Leet: The Leet rule means that characters are swapped for similar characters. So password becomes p@ssw0rd
The researches developed an algorithm during their study which was trained to guess password modifications. Their algorithm was able to guess 30% off passwords within 10 attempts. Taking the reused and modified password pairs, the researchers estimate that 16 million password pairs could be guessed within 10 guesses. After the automated and a manual review, the researchers found that 53.6% off the passwords were matched with either a reused or modified password.
What can you do to stop your password from being guessed or easily hacked?
Use a password management tool such as KeepPass: Password management tools create long, complicated passwords which are securely stored. You don't have to remember them, simply paste them into the login field directly from the app. You can get them as desktop and mobile apps so you can log-in on the go.
Use two-factor or multi-factor authentication: With a second level of authentication required to access certain systems and sites, even when using easy passwords to crack like iloveyou and password123 there is an additional buffer between the hacker and your data.
Need help with your IT support in Leeds? Contact us and our team of IT experts will call you back!
Date published: 29/05/2018

